Azure (24.5 h)
To learn
How to call Microsoft Graph API in B2C app (+3 h)
msal-browser/docs/resources-and-scopes.md
- (todo graph)
- This sample uses the web API registered on Azure AD B2C to get Microsoft Graph API instead of calling MG API via Application Permission (Maybe the latter way doesn't work...).
Add a web API application to your Azure Active Directory B2C tenant
- The scope is defined in your expose APIs
- (todo graph of front end and backend app communication)
msal-browser/docs/working-with-b2c.md
- Users cannot obtain tokens for Microsoft APIs (e.g. MS Graph API) using delegated permissions.
- Applications can obtain tokens for Microsoft APIs using application permissions (user management scenarios).
- to be continued
Differences Between Delegated Permissions and Application Permissions Azure AD - YouTube
- (todo graph)
- (to paste configuration in my playground)
Custom Policy (+10.5 h)
Register a single-page application in Azure Active Directory B2C
OAuth 2.0 Authorization code flow (with PKCE) allows the application to exchange an authorization code for ID tokens to represent the authenticated user and Access tokens needed to call protected APIs. In addition, it returns Refresh tokens that provide long-term access to resources on behalf of users without requiring interaction with those users.
The implicit grant flow allows the application to get ID and Access tokens. Unlike the authorization code flow, implicit grant flow doesn't return a Refresh token.
Tutorial: Create user flows and custom policies in Azure Active Directory B2C
- Create signing key and encryption key under Identity Experience Framework - Policy Keys.
- Register two applications that it uses to sign up and sign in users with local accounts: IdentityExperienceFramework, a web API, and ProxyIdentityExperienceFramework, a native app with delegated permission to the IdentityExperienceFramework app.
- Download policy starter pack and update values of
yourtenant,IdentityExperienceFrameworkAppId, andProxyIdentityExperienceFrameworkAppId. - Upload policy files in correct order.
- Test with B2C_1A_signup_signin. Unfortunately, I got an error:
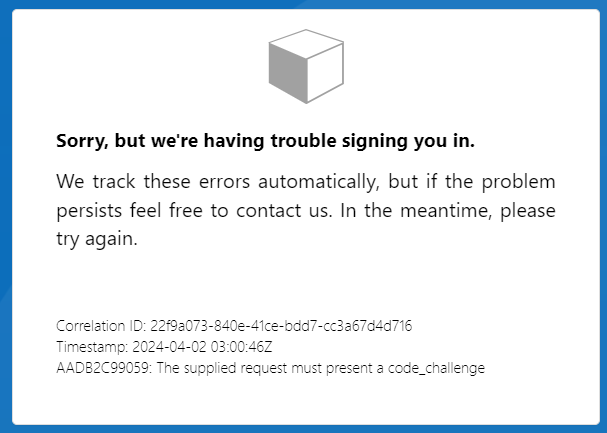 The problem is that I should have used files inside
The problem is that I should have used files inside /Display Controls Starterpack, instead of files under the root.
Write your first Azure Active Directory B2C custom policy - Hello World!
xml<?xml version="1.0" encoding="UTF-8" standalone="yes"?> <TrustFrameworkPolicy xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns="http://schemas.microsoft.com/online/cpim/schemas/2013/06" PolicySchemaVersion="0.3.0.0" TenantId="yourtenant.onmicrosoft.com" PolicyId="B2C_1A_ContosoCustomPolicy" PublicPolicyUri="http://yourtenant.onmicrosoft.com/B2C_1A_ContosoCustomPolicy"> <BuildingBlocks> <ClaimsSchema> <ClaimType> <!-- To declare a claim. A claim is like a variable. The claim's declaration also shows the claim's data type. --> </ClaimType> </ClaimsSchema> </BuildingBlocks> <ClaimsProviders> <!-- Claims Providers Here--> </ClaimsProviders> <UserJourneys> <!-- The user journey specifies the business logic the end user goes through as Azure AD B2C processes a request. --> </UserJourneys> <RelyingParty> <!-- Relying Party Here that's your policy’s entry point Specify the User Journey to execute Specify the claims to include in the token that is returned when the policy runs --> </RelyingParty> </TrustFrameworkPolicy>Set up a password reset flow in Azure Active Directory B2C
Prerequisites: the B2C Users need to have an authentication method specified for self-service password reset. Select the B2C User, in the left menu under Manage, select Authentication methods, ensure Authentication contact info is set. B2C users created via a SignUp flow will have this set by default. For users created via Azure Portal or by Graph API need to have this set for SSPR to work.
Azure AD B2C Webinar Series: Custom Policies Part 1 - YouTube
- User Flow is just built-in policy.
- Claims are just variables.
- Technical Profiles are just functions.
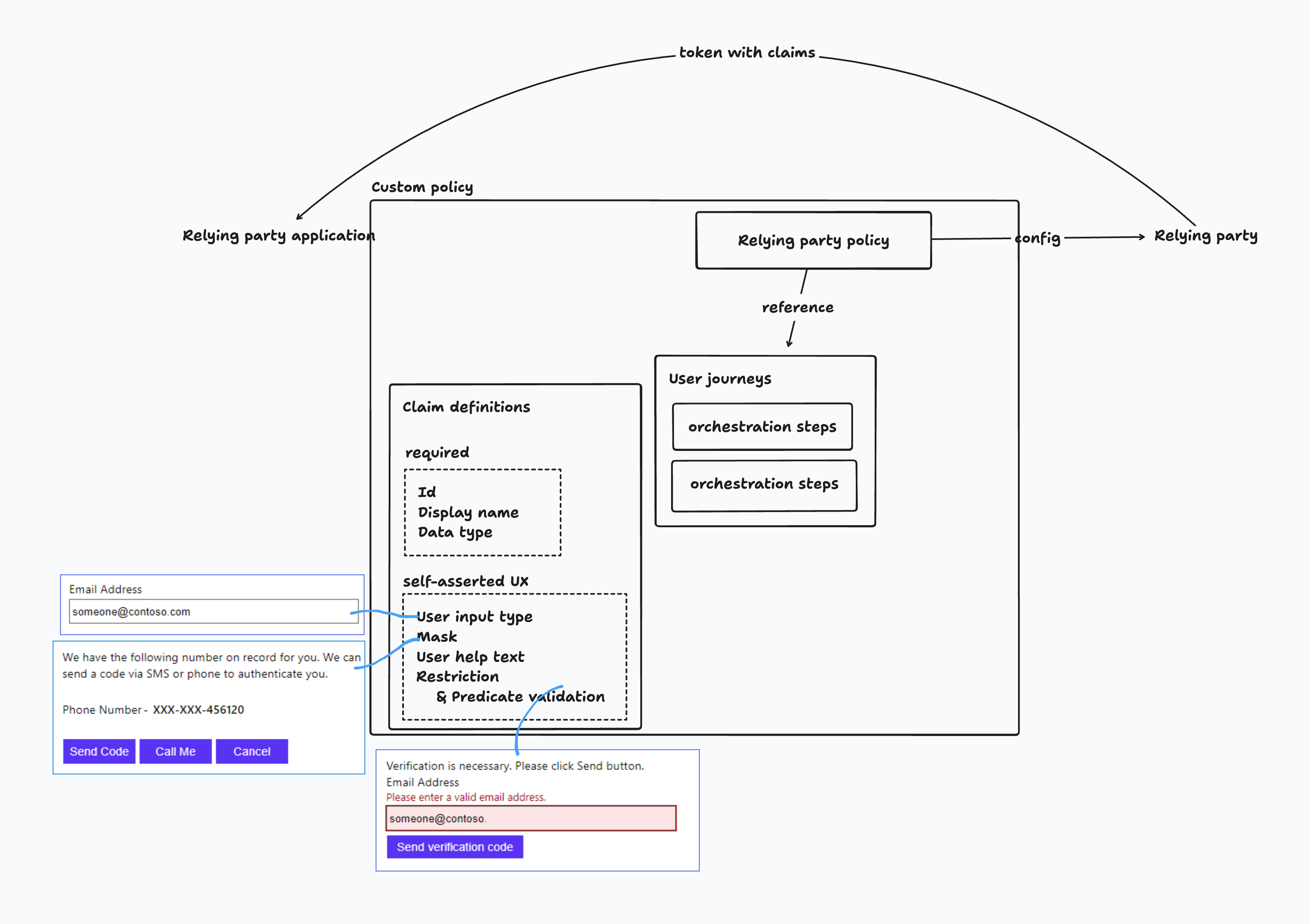 (My understanding of custom policy.)
(My understanding of custom policy.)
Force a password reset after 90 days
- Install the Microsoft Graph PowerShell SDK in Azure Cloud Shell. (Note that Azure AD Powershell for Graph is deprecated.)
- Use Find-MgGraphPermission cmdlet (cmdlets are the native Powershell commands) to check if having the
'Domain.ReadWrite.All'admin. - (todo Option1: connect with scope - delegated permission)
- (todo option2: connect with app secret - app permission)
But I hit a problem that i don't have the permission to connect graph by scope domain.readwrite.all, but Find-MgGraphPermission tells me i have the admin. That's weird. To try: Connect-MgGraph -ClientId <YOUR_NEW_APP_ID> -TenantId <YOUR_TENANT_ID>. if it's not working, switch to free trial.
(todo Connect-MgGraph with application permission) see above
Self-service password reset policies
- (todo cmdlets to check expiration)
- (todo cmdlets to update expiration)
MSAL React (+2 h) (In progress)
redirectUrishould be configured in Azure Portal application authentication. Be careful choose single-page application for type.- All parts of the app that require authentication must be wrapped in the
MsalProvidercomponent. useMsalhook can give us aninstance, and we can dologinPopup,loginRedirect,logoutPopup, andlogoutRedirectwith it. We can also callinstance.acquireTokenSilentto get the tokens (access_token,id_token,client_info,refresh_token, etc), and useaccess_tokento call Microsoft API (e.g Graph API).useIsAuthenticatedhook gives us a boolean value whether or not a user is currently signed-in.
msal-react/docs/getting-started.md:
- Components
AuthenticatedTemplateandUnauthenticatedTemplatecan do the same thing asuseIsAuthenticatedhook does. - Components
MsalAuthenticationTemplateanduseMsalAuthenticationhook can do the same thing asinstancedoes. - Besides of
instance,useMsalgives usaccountsfor an array of all accounts currently signed in, and aninProgressthat tells you what msal is currently doing. - They recommend that the app calls the
acquireTokenSilentAPI on the PublicClientApplication object each time you need an access token to access an API.
- Components
Q: what's the difference between various tokens?
This version of the library uses the OAuth 2.0 Authorization Code Flow with PKCE. To read more about this protocol, as well as the differences between implicit flow and authorization code flow, see the section in the @azure/msal-browser readme.
MSAL Common (+3.5 h)
Two diagrams from my own understanding:
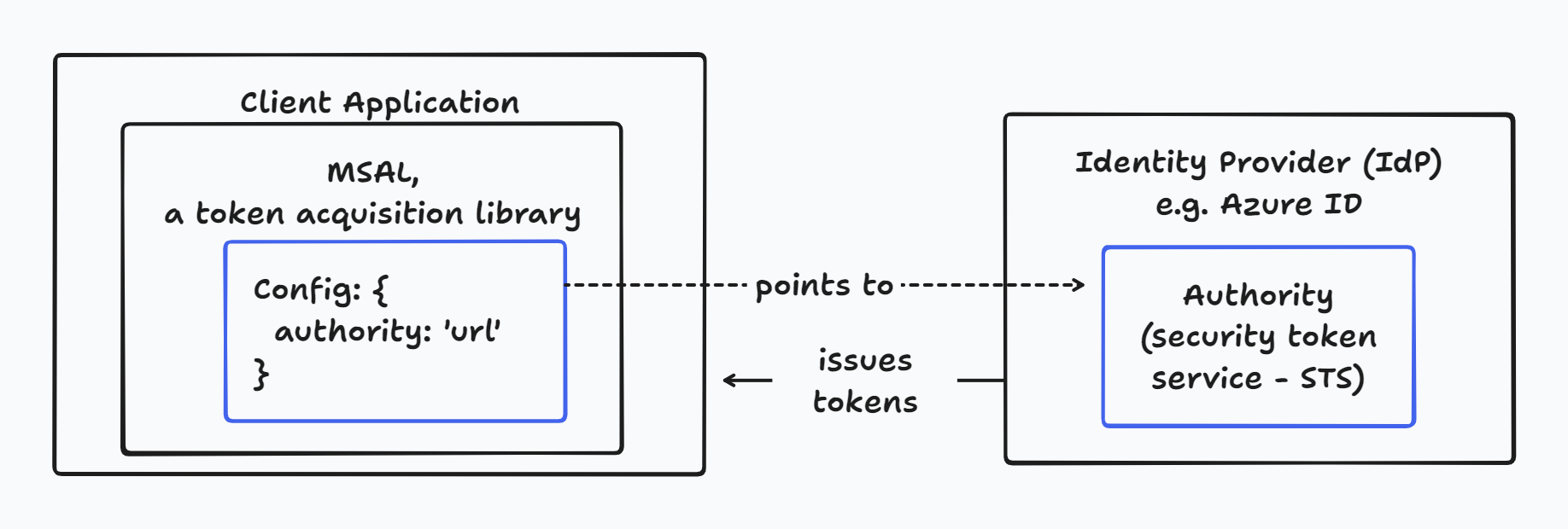
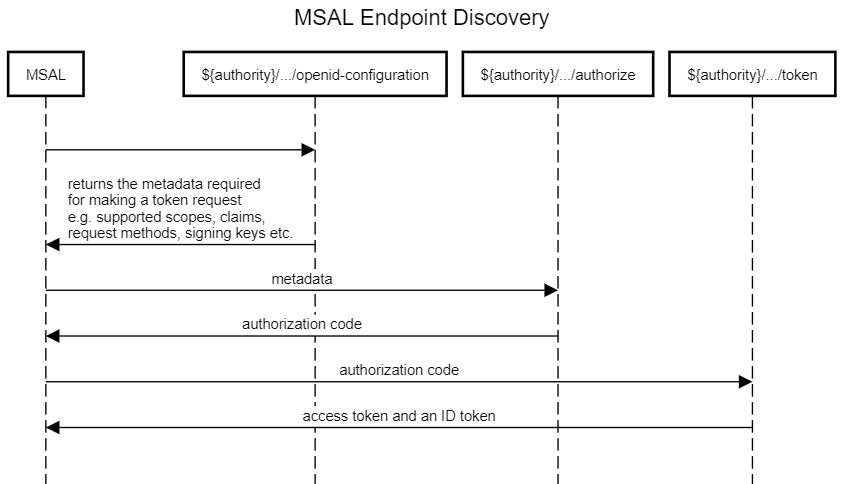
A diagram from the official document:
MSAL Node (+2 h)
Learning materials
What's the difference between Confidential and Public clients? - OAuth in Five Minutes - YouTube
Client = Application
Resource Owner = User
Confidential Clients can keep a secret, and Public Clients can't. Simply put, Confidential Clients are server-side applications (written in Node, Java, etc.), while Public Clients are client-side applications (written in JavaScript, etc).
PKCE (Proof Key for Code Exchange) is an extension to OAuth developed specifically for doing OAuth in Public Clients.
What's the relationship between tenant, subscription, and resource group?
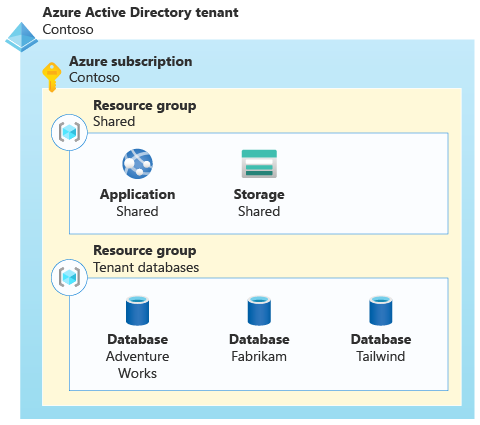
To be continued
Initializing the PublicClientApplication object
Question: how to verify token when requesting
Microsoft identity JavaScript NodeJS tutorial (+2 h)
Getting started with Azure (+2 h)
Identify cloud services
- Infrastructure as a Service (IaaS): Just bare computers (without operating systems). Azure Virtual Machines is IaaS.
- Platform as a Service (PaaS): Hosted platform in the cloud. Not only infrastructure, but also specialized software from the cloud provider, like operating systems. Azure App Service is PaaS.
- Software as a Service (SaaS): software or service hosted in the cloud, e.g. Outlook, Gmail, Netflix, etc
Azure geographies and regions
Countries + Compliance = Geographies
Geographies + Datacenters = regions
3D visualized datacenter: https://bit.ly/gsma-datacenter
E.g. West US is a region, and US is a geography
Azure Resource Manager (ARM)
ARM uses templates to deploy Azure resources. No matter how you interact with Azure or manage your resources, ARM is always going to be doing the work under the hood.
I guess ARM template is like
netlify.tomlwhich is used by Netlify to deploy your application.Azure Blob Storage
- Storing unstructured data
- Organized in containers
- Blob is a file-like object of immutable, raw data.
- Tiers: hot, cool, and archive